When you think about ransomware, malicious attacks on your enterprise systems, and the potential cost of an attack, your PLM system might not be the first thing to pop into your mind. If you’re in the engineering department, you might even consider ransomware nothing more than a nuisance, something for the IT department or your CISO to lose sleep over. However, ransomware attacks don’t ignore the engineering department, and in some cases, malicious actors actively target PLM systems as a critical node of engineering focused organizations.
What to Know About Ransomware
What is Ransomware?
First, let’s be sure to define what we mean when we discuss ransomware. Ransomware is a specific type of malicious software (malware) that employs encryption to hold a victim’s information at ransom. A user or organization’s critical data is encrypted, essentially locking it so that they cannot access files, databases, or applications. A ransom, often cryptocurrency, is then demanded to restore access. Most ransomware is designed to spread itself across a network and target database and file servers, and can thus quickly paralyze an entire organization. It is a growing threat, generating billions of dollars in payments to cybercriminals and inflicting significant damage and expenses for individuals, private businesses, and governmental organizations.
Ransomware usually accesses a network via some sort of phishing scheme. Emails or websites are often disguised to look legitimate, sometimes even like an internal communication, but links or attachments run the ransomware program once clicked or opened. At this point, it is very difficult to stop or slow the attack, as the program is designed to lock out users and then quickly spread across the network. Sometimes, the compromised user will serve as a Trojan horse as the ransomware forwards itself to the attacked user’s contacts, repeating the process and quickly affecting an entire enterprise IT structure.
Why Target PLM Systems?
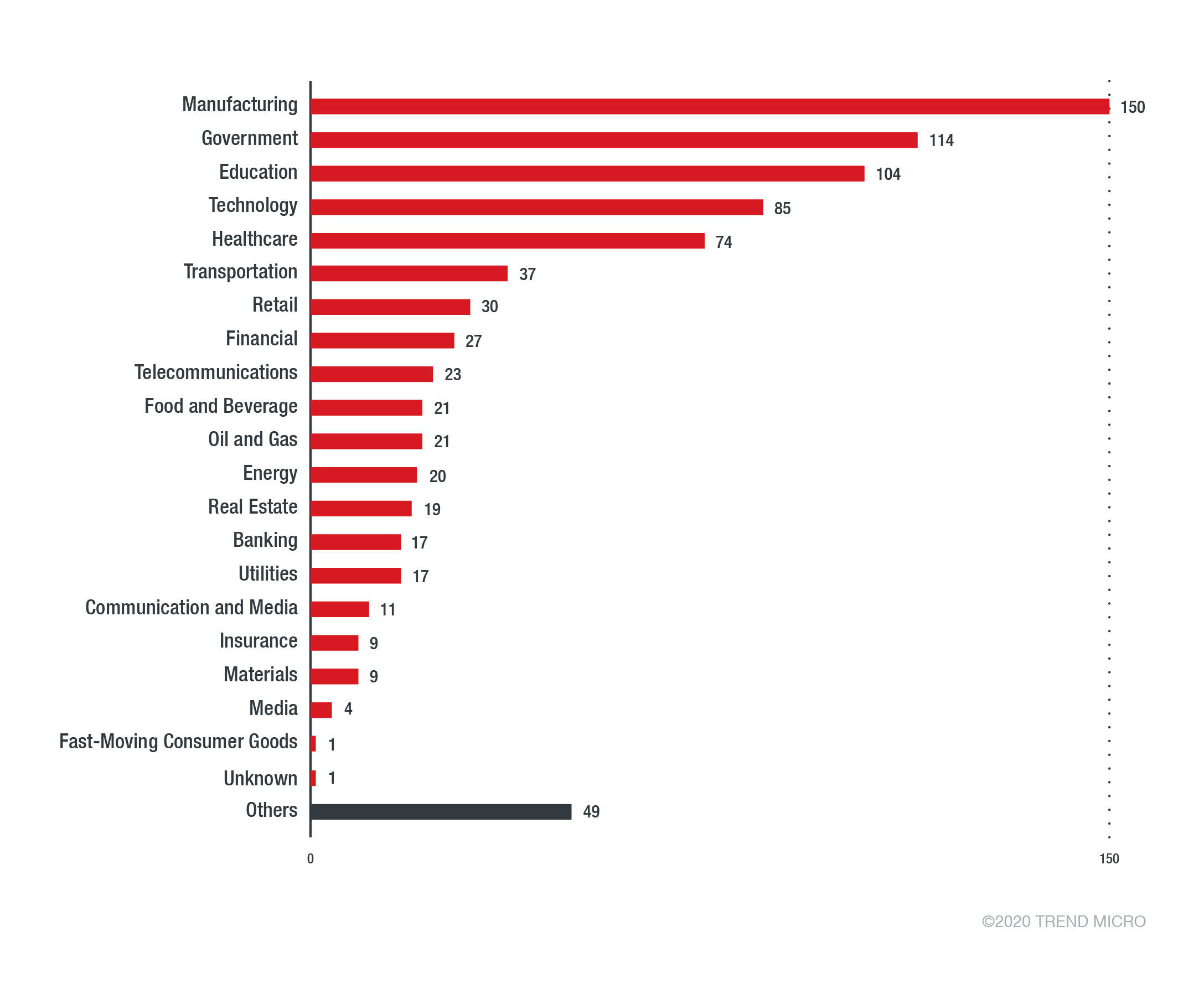
As you can guess by the explanation above, ransomware is not used to attack random targets. Often, malicious actors specifically choose some of the most valuable or vulnerable areas of an organization’s network in order to ensure a ransom is paid quickly and in full. As a hub for your intellectual property, PLM systems are a natural target. Freezing a PLM system affects a number of business units, can slow or halt production, and also puts your IP at risk. Data from Q3 of 2020 shows that manufacturing was the most common target industry for ransomware attacks. It is critical for all manufacturers to be prepared for the possibility of an attack.
What is the Cost of an Attack?
Information Security investment can be costly, but not nearly as expensive as becoming a victim of a successful attack. In a three month span of 2021, the following high-visibility attacks were successfully executed:
March 2021: CNA Financial Corp, one of the largest insurance companies in the US, was locked out of their network for almost two weeks following a breach. CNA ultimately paid $40 million to regain control of its network.
April 2021: An attack on the Houston Rockets NBA franchise resulted in the hackers stealing 500GB of confidential data, including player and staff contracts and NDAs.
May 2021: A cyberattack on Colonial Pipeline forced the company to shut off gasoline supply to much of the Eastern seaboard, resulting in petroleum shortages across a vast portion of the US as people panicked. Colonial paid $4.4 million in ransom to restore their access. Later that month, a separate attack shut down the databases of a hospital system in San Diego for two weeks, blocking access to critical systems and patient records.
June 2021: Multinational meat manufacturer JBS S.A., paid $11 million in ransom following a ransomware attack.
In addition to the financial cost of a ransom, these companies dealt with untold costs in loss of production and loss of credibility. Large-scale incidents like these make headlines, but companies of all shapes and sizes are constantly being probed as potential targets. If you think you’re too small or too insignificant to become a target, think again. Cybersecurity experts estimate that globally, there is one attempted ransomware attack every 11 seconds.
In 2019, Conversant Group, a cybersecurity consulting firm, was engaged with a manufacturing client to overhaul their cybersecurity best practices. While audits and negotiations were happening, the client suffered a ransomware attack by malware known as Mr.Dec. The Mr.Dec attack encrypted and locked almost the entire network, including Epicor (ERP) and Windchill (PLM). As the attack was unfolding, Conversant discovered that the client had been running flawed backups, resulting in a two month gap in the Epicor backup files and no backup for Windchill. The client estimated the time sink to replace the Epicor files at 500 man-hours, costly but reasonable. The Windchill database was a total loss — over 40 years of intellectual property was at risk of vaporizing, an estimated restoration project of 60,000 man-hours, if it was even possible. In the end, a ransom of Bitcoin was paid and all files were eventually restored. You can read a full case study of the incident on Coversant’s website here.
How Do I Protect My Company?
The good news is a smart cybersecurity policy is easy to implement and greatly minimizes the risk of an attack, as well as the costs of a successful breach.
The Human Element
All cybersecurity policy needs to start with people, not tech. A recent study by the IBM Cyber Security Intelligence Index reports shows that 95% of cybersecurity breaches are primarily caused by human error. Training employees to be wary of suspicious emails, websites, and applications is the most important step to keeping your company safe.
Another piece of the human element is to ensure that cybersecurity is clearly demarcated as the responsibility of an individual or team at your company. Some organizations place this under the purview of their IT/IS department, and others have carved out a specific security group led by a Chief Information Security Officer (CISO) or other specialist. There is no right or wrong answer, depending on the size of your company and its information infrastructure, but security must be a priority focus in some form and fashion.
The Technical Element
The next step to minimizing cyber risk is investing in technological safeguards. Top of the line firewalls and antivirus software can help as preventative measures. In the Mr.Dec ransomware case study cited earlier, every layer of the victim’s cybersecurity was flawed, beginning with networks and firewalls.
Additionally, a reliable data backup policy is critical. Systems can be restored with little to no loss of data if backups are thorough and regular. The Mr.Dec victims completely failed to manage this effectively, placing 40 years of IP at risk.
3 HTi is Here to Help
3 HTi is a domain expert in Windchill systems management and engineering. We have assisted customers through cyberattacks, with little to no loss, thanks to our well-established best practices that emphasize security and redundancy. Our services can be as low-touch as a business process audit of your Windchill system or as customized as a full system admin role, managing all aspects of your Windchill environment so that your IT and engineering departments can focus on other items. If you have Windchill data security concerns, contact us today to schedule a conversation to secure your IP.